第 4 節 保安對策
평가된 위협 요소와 취약 요소에 대해서 保安對策(safeguard)을 선택하는 단계 이다.
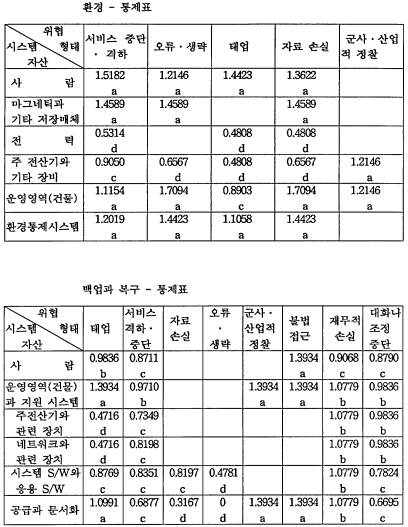
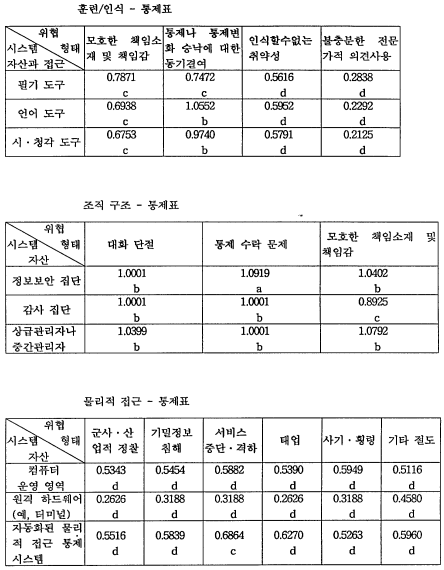
NIST에서 다른 기관에서도 활용할 수 있도록 공표한 보안 지침서인 'SRAG(Simplified Risk Analysis Guidelines)'에서는 위협의 확률과 손실 크기를 5 점척도로서 측정한 후에, 손실 크기가 '매우 높음'인 경우에 한해서 위협의 확률이 '보통' 이상인 경우(즉, '보통', '높음', '매우 높음')에만 保安對策을 마련했다. 본 硏究에서는 통제 수단인 保安對策에 대한 기준을 13개 분야의 각 칸중에서 보안대책이 시급히 필요한 것)로 판정된 것 중 질문에서 'No'라고 답한 항목에서 '매우 높음(VH)'인 질문에 대한 것을 1차적 保安對策으로 제시하였고, '높음(H)'인 항목에 대해서 2차적 保安對策을 제시하였다. H은행 한국 지점의 정보 시스템에 대한 保安對策은 다음과 같다.
1. 1次的 保安對策
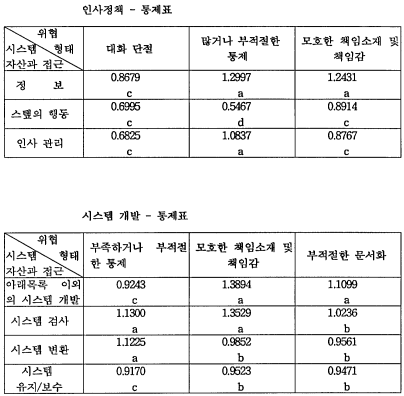
1) 인사 정책
●스텝 행동:많거나 부적절한 통제
-임시 고용인, 컨설턴트, 계약업자 등의 다른 비직원이 중요한 위치에 있을 때 직원과 동등한 신원 조회 같은 보안 규정을 적용한다.
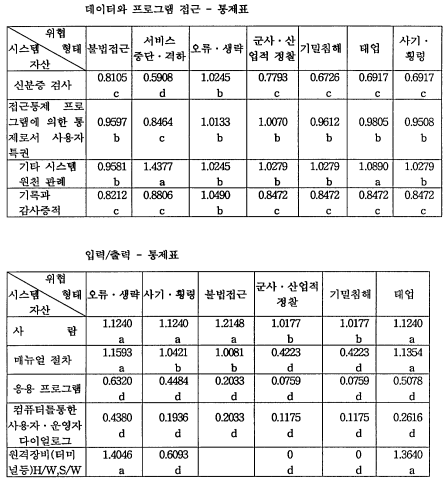
2) 데이터 와 프로그램접근
●신분증 검사:서비스 중단 · 격하
패스워드의 발행은 사용자와 직속 상관의 인가에 의한 신청에 근거하도록 한다.
3) 입/출력
● 메뉴얼 절차:군사,상업적 정찰,기밀침해
응용프로그램:군사 ·산업적 정찰, 기밀침해 민감한 하드카피 보고서의 각 페이지마다 적합한 데이터 보안 등급 (classification)을 표시한다.
●매뉴얼 절차:군사 ·산업적 정찰, 기밀침해 특별히 민감한 하드카피 출력은 로그를 통해 추적가능하며 그 출력물에 복사가 금지되며 이런 복사물의 발견 시 중앙에서 이런 출력을 관리하는 사람에게 보내져야 한다는 내용을 표시한다.
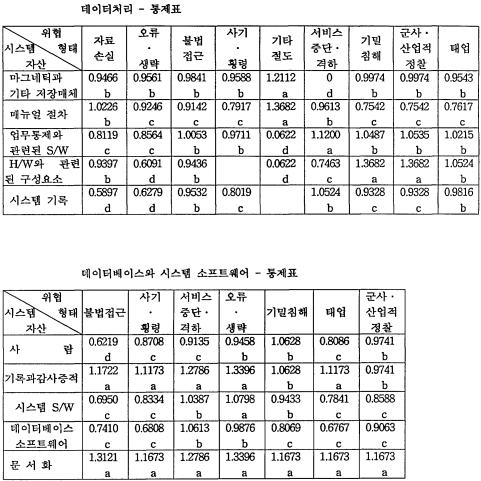
4) 데이터 처리
●시스템 기록:자료손실, 오류 · 생략
-오퍼레이터 콘솔 로그가 하드 카피에 기록됨은 물론이고 테이프 또는 다른 매체도 기록한다.
5) 데이터베이스와 시스템 소프트웨어
●사람:불법접근
-공급자가 dial-up line을 통해 진단과 유지보수를 행할 경우, 특정 port만 사 잘하고 전산 운영 책임자로 부터 허가를 받은 후에 사용하도록 한다.
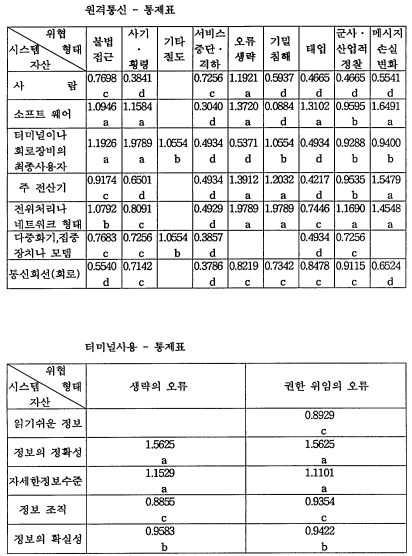
6) 원격통신
●소프트웨어:서비스 중단,격하
전위처리나 네트워크 형태:서비스 중단,격하
통신회선(회로)서비스 중단,격하
-네트워크의 일부가 고장이거나 작동 불능일 경우, automatic traffic rerouting 과 같은 기능을 사용하여 데이터 통신이 자동으로 지속될 수 있도록 통신 시스템을 설계한다.
●소프트웨어:서비스 중단,격하
터미널이나 회로장비의 최종사용자:서비스 중단,격하
주 선산기:서비스 중단,격하
전위처리나 네트워크 형태: 서비스중단,격하
다중화기,집중장치,모뎀:서비스 중단:격하
- 중요 네트워크 장비가 작동 불능일 경우,네트워크 노드와 주 전산기는 대기중인 여분의 장비로 자동 교환할 수 있도록 항상 준비한다.
7) 백업과 복구
●주 전산기와 관련장치, 네트워크와 관련장치:태업
- 주 데이터처리 지역에서 특별한, 주문 제작된, 또는 구입하기가 힘든 장비가 사용되고 있다면 이들 장비를 백업지역에도 설치한다.
정보시스템 13개 분야 중 시스템 개발, 조직 구조, 터미널 사용을 제외한 10개 분야 중 1차적 보안대책은 인사정책, 데이터 및 프로그램 접근, 입/출력, 데이터 처리, 데이터베이스와 시스템 소프트웨어, (원격)통신, 백업과 복구 분야에서 나타났고, 1 차적 보안대책이 실행된 후에 2차적 보안대책을 실시해야 한다.
2. 2次的 保安對策
1) 훈련/인식
●필기, 언어, 시 ·청각도구:인식할 수 없는 취약성,불충분한 전문가의견 사용
- 통제 절차를 설계하는 시스템 설계자나 다른 기술직 직원들을 정보 보호 교육에 참여 시켜 그들의 통제(관리)에 관하여 논의할 수 있는 기회를 제공한다.
●필기 도구:인식할 수 없는 취약성
- 정보 보호에 관련된 문서들을 검토해서 너무 많은 정보가 누출되지 않도록 검토한다(시스템에 침입하고자 하는 사람은 때때로 필요한 모든 정보를 관련 문서 혹은 온-라인으로 얻을 수 있다)
2) 물리적 접근
●컴퓨터 운영영역:군사 ·산업적 정찰, 기밀정보 침해,서비스 중단 ·격하, 태업, 기타절도
-제한된 정보 통제 영역에 24시간 출입을 감시하는 경비원을 채용한다.
● 컴퓨터 운영영역서비스 중단·격하, 태업, 기타절도
- 경비원이 제한된 정보 통제 영역 및 빌딩내의 기타 제한 구역을 순찰하도록 한다.
● 컴퓨터 운영영역:태업, 기타절도
- 제한된 정보 통제 영역의 출입구에 폐쇠회로(CCTV)를 설치(작동)한다.
● 자동화된 물리적 접근 통제시스템:군사 ·산업적 정찰, 기밀정보 침해, 태업,사기 ·횡령, 기타절도
-퇴직한 또는 다른 비인가자들이 비록 아직 까지도 신분증이나 유사한 식별표시 를 가지고 있다 하더라도 접근을 거부할 수 있는 물리적 접근 통제 시스템을 설치한다.
● 컴퓨터 운영영역:군사 ·산업적 정찰, 기밀정보 침해, 서비스 중단 ·격하, 태업, 사기 · 횡령, 기타절도
-모든 출입증에는 사진을 부착한다.
● 컴퓨터 운영영역:군사·산업적 정찰, 기밀정보 침해, 서비스 중단·격하, 태업, 사기 · 횡령, 기타절도
원격 하드웨어:군사 ·산업적 정찰, 기밀정보 침해, 서비스 중단·격하, 태업, 사기·횡령, 기타절도
자동화된 물리적 접근 통제시스템: 군사 ·산업적 정찰, 기밀정보 침해, 태업, 서비스 중단 ·격하,사기 ·횡령, 기타절도
-제한된 정보 통제 영역에 인가된 사람이 없을 때 보호를 위한 자동 도난 경보 장치를 설치한다.
3) 데이터와 프로그램접근
● 신분증 검사:서비스 중단·격하 패스워드를 잊어버린 사용자들이 새로운 패스워드를 전화상으로 받을 때 새로운 패스워드를 주는 보안 담당자는 그 사용자들의 신원을 명확하게 확인하는 적절한 절차하에 실행한다.
- 패스 워드들이 터미널 주변에 부착되어 있든지 혹은 권한이 없는 사람들에 의해 발견되기 쉬운 곳에 방치되지 않도록 한다.
- 엄격하게 금지된 패스워드를 다른 사용자에게 누설함으로써 한 패스워드가 여러 사람에 의하여 사용하는 것을 엄격하게 금지시킨다.
4) 입/출력
● 응용프로그램:사기 · 횡령
-중요하거나 민감한 거래 처리는 정상적 처리 절차와는 별도로 별개의 시리얼 넘버의 사용과 같이 특별한 절차로 통제한다.
● 응용 프로그램:오류,생략,사기,횡령,불법접근
사용자·운영자 다이얼로그:오류·생략
- 입력 배치(batch)나 거래 입력이 일단 시스템 내로 들어가게 되면, 입력이 거절된 것을 제외하고는 입력 데이터의 변경을 금지하고 예방한다.
● 메뉴얼 절차:군사,산업적 정찰,기밀침해
응용프로그램:군사,산업적 정찰,기밀침해
-모든 출력물에는 수취인의 이름이 포함되고, 이러한 출력물의 분배는 단지 해당 사람에게로 제한한다(via locked bins, couriers, ell.).
● 원격장비 하드웨어와 소프트웨어:군사 ·산업적 정찰, 기밀침해 터미날 상에 민감한 출력물이 나타날 때 관련 데이터의 보안 등급을 표시한다.
● 매뉴얼 절차:군사 ·산업적 정잘, 기밀침해 만약 특별히 민감한 출력이 추적되면, 굴력의 복사물에 일련 번호가 부과되고 모든 복사물은 사용 후 반드시 되돌려 받는다.
● 매뉴얼 절차:군사,산업적 정찰,기밀 침해
원격장비 하드웨어와 소프트웨어:군사,산업적 정찰,기밀침해
-기밀침해 복사 먹지(carbon paper)가 어떤 민감한 출력 업무에 사용되어지면 이 복사 먹지를 보안적인 태도(절단, 소각 등)로 처리한다.
5) 원격통신
● 통신회선(회로):불법접근
- Dial-up을 통해 비인가된 자가 접근함을 방지하기 위해, 점대점, multidrop, LAN, 다른 통신 구조는 사용자로 하여금 특정 물리적 장소에 국한시키는 제약조건을 마련한다.
- Dial-up 회선을 통해 통신할 때, 자동 call-back 장치가 사용되어 사용자가 세션을 시작하고자 할 때 필요한 정보를 입력한 후 미리 지정된 번호로 전화가 되돌아 오도록 한다.
6) 백업과 복구
● 시스템 소프트웨어와 옹용 소프트웨어:오류 · 생략
- 응용프로그램이 정확하게 데이터를 처리하는지를 확인하는데 사용할 수 있도록 각 중요 응용프로그램의 테스트용 데이터와 특정 테스트절차를 다른 중요한 자원(material)들과 합께 off-site에 보관한다.
2차적 보안대책은 훈련/인식, 물리적 접근, 데이터 및 프로그램 접근, 입/출력, (원격)통신, 백업과 복구에서 나타났다. 정보시스템 13개 분야 중 보안대책이 필요한 10개 분야에서 환경 분야의 전력에 관계한 보안대책이 필요한 것으로 나타났으나 사례회사의 경우는 전력에 대한 보안대책이 필요하지만 전력의 경우는 임대건물에서 일괄적으로 통제를 하기때문에 회사 자체적으로 대책을 수립하는 것이 어렵기 때 문에 기술하지 않았다.
第 5章 結 論
第 1 節 結 論
위험관리란 危險分析과 保安管理로서 구성되어있다. 危險分析이란 정보시스템과 그 자산의 기밀성, 무결성, 가용성에 영향을 미칠 수 있는 다양한 위협에 대해서 시스템의 취약성을 인식하고, 이로 인해서 예상되는 손실을 分析하는 것이다. 危險分析과정은 자산, 위협, 취약성, 保安對策, 그리고 손실를 계산하는 여러요소들 간에 관계를 分析하는 것이다. 保安管理란 危險分析에 의해서 선택된 保安對策을 설치해서 유지j보수하는 것이다. 危險分析方法에는 위협발생확률과 손실크기를 곱해서 계산하는 '기대가치분석 (expected value analysis)'인 정량적분석법과, 손실크기를 화폐가치로 측정할 수 없어서 危險을 기술변수(descriptive variables)로 표현하는 정성적분석법이 있다. 정 량적 분석법에는 수학공식접근법, 확률분포추정법, 점수법, 몬테칼로 시뮬레이션, 확률지배, 과거자료접근법 등이 있고, 정성적분석법에는 델파이법, 시나리오법, 순위결정법, 퍼지행렬법, 질문서법 등이 있다. 그리고, 복합적인 분석법으로 가치사슬 분석 이 있다. 정보시스템 危險分析을 위한 保安설계방법이 3가지 세대로 진화되고 있다. 제1 세대 방법인 체크리스트 접근방법은 보안대책의 유무에 대한 질문서로서 危險分析 중에서 특히 문제와 해의 공간을 압축시키는 것이다. 취약성은 보안대책의 결핍상 태로 정의되고:취약성 평가를 保安對策의 유무를 식별하여, 保安對策이 결핍상태 에 있는 경우 위협발생을 감소시킬 수 있는 保安對策을 제시하는 것이다. 保安의 영역은 일반적으로 물적 보안, 논리적 보안, 경영 보안으로 구분된다. 체크리스트 접근방법에는 'SAFE 체크리스트', '컴퓨터 보안편람', '컴퓨터 보안 자체 감사를 위한 AEES 체크리스트', LLNL 체크리스트' 등이 있으나, 이 중에서는 'LLNL 체크 리스트'가 상대적으로 물적/논리적/경영 보안에 대한 평가항목이 합리적으로 구성 되어 있다.
LLNL체크리스트를 이용한 事例硏究의 주요 결과는 다음과 같이 요약된다.
첫째, 시스템 개발, 조직 구조, 데이터 베이스와 시스템 소프트웨어, 터미널 사용, 환경 분야에 대한 保安對策이 잘되어 있어 현상태로 충분한 것으로 나타났다. 이는 시스템 개발과 데이터 베이스와 시스템 소프트웨어 분야의 경우는 한국 지점 에서 요구하는 것을 본사에서 직접적이고 체계적으로 관리하기 때문이고, 조직 구조와 환경 분야는 한국 지점의 경우 조직 구성원과 정보시스템의 자산이 작아 관리와 불만 다각적으로 수용할 수 있고, 터미널 사용 분야도 조직 구성원이 작기 때 문에 터미널 사용에 대한 감독을 수월하게 할 수 있기 때문이라 사려된다.
둘째, 인사 정책, 훈련 및 지각, 데이터와 프로그램 접근, 입력 및 출력, 데이터 처리, (원격)통신, 백업과 복구 분야는 保安對策이 아주 시급히 필요한 것은 아니나 기존의 保安對策으로는 취약하여 保安對策이 필요한 것으로 나타났다. 이중 (원격) 통신, 입력 및 출력 분야의 경우는 사례회사가 은행이라는 점을 고려하여 다른 분 야에 우선하여 保安對策을 마련해야 될 것으로 사려된다.
세째, 물리적 접근 분야는 자동화된 물리적 접근 통제 시스템에 대한 지속적인 서비스 문제를 제외하고는 모든 부분에 있어서 시급한 保安對策을 마련해야 될 것으로 나타났다. 이는 사례회사가 은행이라는 특수성으로 인해 시스템의 자산이 외부로 노출이 쉽기 때문에 위협에 대한 보안대책 수립이 어렵기 때문인 것으로 사려된다.
본 硏究의 시사점은 정보화의 급속한 발전에도 불구하고 우리나라의 경우 대부분의 기업에서 정보시스템 보안에 대한 체계적인 대책이 없는 실정이어서 향후 우리나라 실정에 맞은 소프트웨어 분석 방법 개발을 위해서는 본 硏究가 필수적 이다.
第 2節 硏究의 限界 및 向後 硏究課題
본 硏究의 한계점을 몇 가지로 요약함으로 앞으로 정보시스템 保安에 관한 취 약성 평가 및 危險分析에 대한 硏究方向을 제시해 보면 다음과 같다.
첫째, 설문지의 응답자 설정의 문제에서 개인적인 인식의 문제에 따라 달라질 수 있으므로 직급과 경험이 풍부한 전문가로 하고 주관을 줄이기 위해 여러 사람의 질문을 통합하여 분석하는 것이 바람직하다.
둘째, 危險分析方法들은 정확성, 완전성, 노력, 실행성, 이용기술, 지원가능성, 측정가능성 등 선택 기준들과 분석 방법들의 장·단점을 고려해서 위험 분석자 흑은 경영자는 특정 상황에 적절한 분석방법을 선택해야 한다. 위험분석과정에서 정량적 분석법이 정성적 분석법보다도 선택기준 측면에서 우수한 방법이지만, 별로 이용되지 않은 이유는 주관적 성질을 갖고 있는 위험을 계량화하는 데는 한계가 있기 때문이다.
세째, 위협의 발생빈도가 매우 작은 경우나 손실크기를 화폐 가치로 추정해야 하는 경우 충분한 과거자료가 없는 경우가 대부분이다. 무엇 보다도 危險分析方法 의 불완전성과 의사결정자의 제약된 합리성이 危險을 분석하는데 가장 큰 한계점 이 된다. 그러므로, 선택기준을 고려해서 그 분석방법을 선택하되 가능하면 여러방법을 복합적으로 사용하는 것이 바람직하다.
네째, 체크리스트 접근 방법은 정보시스템 자산과 위협과의 관계에서 현 시스템의 보안 수준만을 나타내므로 위협의 발생확률과 손실의 크기를 계량적으로 계 산할 수 업어 정보시스템에 대한 위험 측정과 제시된 보안대책의 費用1效果 分析을 할 수 없다. 그러므로 완전한 危險分析의 틀이 될 수 없는 한계가 있다. 완전한 危險分析 틀이 되기 위해서는 정량적으로 위협의 발생확률과 손실의 크기를 측정할 수 있는 정량적인 危險分析方法을 병행해야 한다. 다섯째, 本 硏究에서 사용한 LLNL 체크리스트의 질문 내용 854개 중 우리 실정에 맞지 않은 항목을 제외시킨 784개 항목에 대한 분석을 실시하였으나 새로 운 상황에 맞는 항목을 추가 시키지 못했다. 앞으로 체크리스트의 항목을 정보시스템 변화에 따라 계속적인 수정이 필요하다.
여섯째, 체크리스트의 결과 분석에서 본 연구는 H은행의 한국지점 단일 기업에 대해서 실시하여 다른 조직과의 상대적 수준 비교를 하지 못하였다. 차후 연구 에서는 동종 기업이나 동종 산업별로 비교하여 상대적 수준을 제시하는 것도 중요 하다.
마지막으로 정보시스템 危險分析에 대한 우리나라 실정에 맞는 危險分析 模型 을 개발하여 소프트웨어화 하는 것이 필요하다.
참 고 문 헌
<國內文獻>
김 기 윤, "정보기술에 대한 위험분석방법," 기업경영연구, 제 3권, 광운대학교 기업경영 연구소, 1994, PP. 1-18.
김 기 윤, 김 정 덕, "정보시스템 위험분석과 관리," KMIS'94추계 학술대회 논문집, 한국경영정보학회, 1994, PP. 277-297.
<日本文獻>
コンピヱ- タセヱリィに關する リスワ 분석 (JRAM にるアプロ-チ), 日本情報處理開發協會, 平年 4, pp. 33-44.
<歐美文獻>
Charles C. Wood, William W. Banks, Sergio B, Gualro, Abel A. Garcia, Victor E. Hampel and Henry p. Sartorio, "Computer security," A Willey-Interscience Pliblication, 1987. Commission of the European Communities Security Investigations Projects, Risk Analysis Methods Database, Project S2014 - Risk Analysis, Report Number 19744(S2014/WP08), Version 1.0, Jan. 1993.
Commission of the European Communities Security Investigations Projects, final and Strategy Report, Project S2014 - Risk Analysis, Report Number 9744(S201VWP08), Version 1.0, Feb. 1993.
Cooper, J. A., Computer 8T Communications Security Strategies for 1990s, McGraw-Hill, 1989.
FIPS PUB 41, Computer Security Guidelines for Implementing the Privacy Act of 1974, U.S. Department of Commerce/National Bureau of Standards, May. 1975.
FIPS PUB 65, Guidelines for Automatic Data Processing Risk Analysis, V.S. Department of Commerce/National Bureau of Standards, Aug. 1979.
FIPS PUB 73, Guidelines for Suwi.5 of Computer Applications, U.S. Department of Commerce/national Bureau of Standards, Jun. 1980.
Guairo, 5., "Analytical and Decision Models of the Livermore Risk Analysis Methodology(LRAM)," Proceedings of the 1988 Computer Security Risk Management Model Builders Workshop, 1988, pp.49-72.
Gilbert, 1. A.,"Risk Analysis: Concepts and Tools," Datapro Reports on Information Suwity, Risk Analysis, Sep. 1991, pp.101-112.
ISO/TEC JTC1/SC27 N689, Guidelines for the Management of IT System Security: Part3-Techniques for the Management of IT Security, ISO, Mar. 1993.
ISO/TEC JTC1/SC27 N72O, Guidelines for the Management of IT Security (GMITS): Part2-Managing and Planning If Security, 150, May. 1993.
ISO/TEC JTC1/SC27 N777, Guidelines for the Management of IT System Security(GMITS): Part1-Concepts and Models for IT Security, ISO, Oct. 1993.
ISO/TEC JTC1/SC27 N442, Key Management PUI: Framework, 150, Mar. 1994.
Katzke, 5., "A Government Perspective on Risk Management of Automated Information Systems," Proceedings of the 1988 Computer Security Risk Management Model Builders Workshop, 1988, pp.3-20.
Moses, R., "Risk Analysis and Management," Computer Security Reference Book edited by Jackson, K. M.8f Hruska,1.8E Parker, Dom B., CRC Press, Inc., 1992, pp.227-263.
"CCTA Risk Analysis and Management Methodology(CRAMM)," Datapro Reports on Information Security, December 1992, pp.101-110. NIST, V.S. Department of Justice Simplified Risk Analysis Guidelines, HISTIR 4387, Aug. 1990.
Otwell, K. and AAdiiage,3., "The Role of Vulnerability in Risk Management," Computer Security Journal, Vol.W, No.1, 1989, pp.15-21.
Ozier, W., "Issues in Quantitative Versus Qualitative Risk Analysis," Datapro Reports on Information Security, Risk Analysis, March 1992, pp101-107.
Perry, W.S,8f Kuong, J. F., EDP Risk Analysis and Control Justification, Management Advisory Publications 1981. Ruiner, R. J. Jr.5f Snider, C. A.8. Cair, H. H., Risk Analysis for Information Technology, loan of Management Information Systems, 1991, Vol.8, No.1, W.129-147.
Richard Baskerville, "Information System Security Design Method: Implications for Information Systems Development," ACM Computing Surveys, Vol. 25, No. 4, December 1993.
Robak, E. EE Security and Emergency Planning Staff, U.S. Department of Justice Simplified Risk Analysis Guidelines(SRAG), National Institute of Standards and Technology, 1990.
Schmidt E.,"Conceptual Model of the Risk Management Process," Proceedings of the 1988 Computer Security Risk Management Model Builders Workshop, 1988, PP.89-102.
System Security Study Committee, Computer Science and Telecommunication to Board, Commission on Physic誠 Sciences, Mathematics, and Applications, National Research Council, "Computers at Risk," National Academy Press, 1991.
Von Solms, R. and Eloff, J. H. p. and von Solms, 5. H., "Computer security management: a framework for effective management involvement," Information Age, Vol.12, No.4, Oct. 1990, pp.217-222.
William E. Perry and Javier F. Roung, "EDP Risk Analysis and Controls Justification," Management Advisory Publications, 1981.
부록:정보시스템 13개분야의 통제표