정보시스템 취약성 평가 : 체크리스트 접근방법
국문요지
정보시스템 취약성 평가; 체크리스트 접근방법(ABSTRACT)
Vulnerability Assessment for IS: Checklist Approach
Jong Seok, Kim Department of Business Administration The Graduate School, Kwang Woon University
As Information System (IS) has become increasingly important In the competitive position of firms, managers have grown more sensitive to their organization's overall IS risk management. In an attempt to minimize or avoid such losses, managers are employing various qualitative and quantitative risk analysis methodologies. Any loss of confidentiality, integrity or availability in terms of information security may have impact on the capability of an organization to carry out its business. risk unysis is the Process managers use to examine the throats facing their IS assets and the vulnerabilities of those assets to the risk. Risk analysis consists of identifying Information System assets, identifying threats to those assets and determining the vulnerability of asset(s) In threat(s) and establishing the appropriate security safeguards for a system.
The concept of vulnerability plays an important role in risk analysis for information systems. In general, vulnerability is defined as three ways: 1) as an attribute of assets, 2) as a relationship between assets and threats, 3) as the absence of safeguards or controls. In this paper, we define vulnerability as the absence of safeguards or controls. This paper proposes case study for vulnerability assessment using LLNL checklist approaches and provides safeguards for IS. This paper consists of five chapters as follows
The first chapter descrives the purposes, methodology, scope for this study. The second chapter reviews the existing approaches using checklist for IS vulnerability. We descrive the concept of risk/security management procedure of risk analysis and 삼le vulnerability assessment for IS.
The third chapter descrives a general procedure of IS risk analysis and introduces several methods using checklist approach and software approach for IS vulnerability assemest, as well as LLNL checklist structure.
The forth chapter is to examine IS vulnerability assessment. We descrive current information system environment prior to comprehensive risk analysis it is essenti刻 to determine what constitutes the IS environment of an organization in terms of hardware, software, humanware and data. We assess IS vulnerability and suggest safeguards.
The fifth chapter summaries conclusion and suggests limitation of this study and future study.
The purpose of this paper is to provide an analytical description of IS vulnerability assessment and safeguard. This paper is not in intended to a generic solution for any situation the case must be examined on its own merits and appropriate actions selected. Major implication of this study suggests a conceptual/practical foundation for Risk Analysis of Information Technology (Information System) .
Key Words: Information system(151, Information Technology, Risk Management, Risk Analysis, Vulnerability Assessment, Security, Checklist Approach, Safeguard
第 1 章 序 論
第 1 節 硏究目的
80년대에 들어서면서 정보통신이나 자동화 등의 영역에까지 다양한 기술과 서비스를 제공해 주기 시작하면서 컴퓨팅(computing)의 새로운 시대가 시작되었고 이 를 정보기술시대(Information Technology Era)라 부르게 되었다. 정보기술은 기업 이 추구하는 목적을 달성하는데 필요한 기술을 제공해 주는 컴퓨터 하드웨어, 소프트웨어, 데이터는 물론 통신시스템과 네트워크를 포함하고 또한 이들이 제공하는 새로운 서비스까지를 통칭하는데 정보시스템이라고도 한다.
정보기술시대에서는 정보가 재화로서의 가치를 인정 받으며 컴퓨터와 전산망을 통하여 유통되는 정보량이 대량화 되고 사회전반에 미치는 정보의 역할이 가장 중요하게 인식된다. 우리 나라에서는 행정전산망을 시점으로 해서 국가 기간 전산망이 확대되어 정착되어 가고 있으며 한국통신, 데이콤 등의 공중 통신망 사업자들에의 한 다양한 정보 서비스가 더욱 가속화되고 있다. 우리 정부는 국제경쟁력을 향상시키기 위한 정보 고속화 전산망 구축을 추진하고 있으며 정보사회에서는 정부기관 뿐만 아니라 모든 기간 산업체들도 컴퓨터와 통신기술을 포함하는 정보시스템(정보 기술:Information Technology)에 의존하여 업무를 수행할 수 밖에 없는 환경으로 변모되고 있다.
이와 함께 중요한 정보에 대해서 비밀성, 무결성, 가용성이 상실될 때는 사업을 수행하는 조직의 역량에 심대한 영향을 미치게 됨에 따라 정보시스템에 대한 保安 管理 體系가 절실히 요구된다. 그러나 지금까지 정보시스템은 통합된 시스템의 관점에서 보다는 부분적인 관심 분야에만 역점을 두어 개발되고 관리되어 왔으며 정부기관 및 민간사회 전체를 대상으로 하는 국가적인 차원에서의 保安管理가 소홀하 였다고 볼 수 있다. 이제는 정보보안이라는 용어의 특수성에 적합한 정보시스템 危險管理가 이루어질 수 있도록 체계적인 硏究가 수행되고 이를 뒷받침할 수 있는 조직과 제도가 구축되어야 할 시점에 도달하였다고 본다. 정보시스템 危驗管理는 정 보가 생산, 처리, 전달 및 저장되고 다시 폐기되는 정보 시스템의 순환과정에서 정보에 대한 보안이 이루어지도록 관리하는 것이다.
본 硏究의 의의로서는 정보시스템의 危險分析을 위해 첫째, 정보시스템의 保安 을 위한 危險分析을 위한 (保安)설계방법을 분류하고, 둘째, 기존의 정보시스템의 취약성평가를 위한 체크리스트의 체계를 기술하고, 세째, 事例硏究를 통해 wood et al(1987)이 주장한 LLNL 체크리스트 법을 통하여 취약성을 평가하고, 네째, 사례 회사의 보안대책을 제시함으로써 향후 정보시스템 保安 분야의 이론적 ·실무적틀을 제공하고자 한다.
第 2 節 硏究方法
본 硏究는 사례조사를 통하여 정보시스템의 자산 및 위협 요소들을 파악하고 정보시스템의 취약성을 식별하고 평가하여 保安對策을 제시하기위한 탐색적 硏究 (Exploratory research)이다. 事例硏究를 위해서는 외국은행의 보안담당 전문가에게 의뢰하여 현재 정보시스템의 현황을 파악하기 위한 정보시스템의 일반사항에 대한 질문과 정보시스템의 위험실태를 평가하기 위한 질문을 실시하였다. 정보시스템 위험실태 평가 질문은 정보 시스템의 保安에 관련된 LLNL체크리스트 857개 항목에서 우리나라 실정에 맞지않는 항목을 제외시켜 수정한 후, 784개 항목에 대해 조사하였다.
정보시스템 현황파악을 위한 질문은 회사의 전반적인 상황 및 응답자에 대한 사항을 개방형 질문(open-ended question)을 통하여 측정하였고, 정보시스템 취약성 실태 평가를 위한 질문은 인사정책, 시스템 개발, 훈련1인식, 조직구조, 물리적 접근, 데이터와 프로그램 접근, 데이터 입1출력, 데이터 처리, 데이터베이스와 시스템 소프트웨어, (원격)통신, 터미널 사용, 환경, 백업과 복구 등의 13개 분야의 체크리스트로 나누어 질문을 체크리스트 방식을 통하여 측정하였다.
체크리스트를 통하여 측정된 질문은 각 문항마다 아주 높음(VH), 높음(H), 보통(M), 낮음(L), 아주 낮음(VL)의 5등급으로 가중치를 부여해 각 분야에서 위협형태 및 시스템 자산과 시스템 접근방법에 따라 통제표를 만들어 통제표의 각 셀(cell)마다 가중비율지수(W), 적용지수(AS), 조정지수(AS), 최대점수(MPS)를 계산하여 전 체 통제지수(CCI)를 산출하여 현재 시스템의 통제 정도를 측정하였다.
第 3 節 硏究範圍
정보시스템 취약성 평가에 관한 硏究는 정보시스템과 정보시스템의 保安 정책 에 대한 폭넓은 접근을 필요로 한다. 이러한 접근은 정보시스템 관리자의 保安 징 책에 대한 전문가적 의견을 통해 이루어 진다. 본 硏究는 다음과 같은 범위 내에서 접근하고자 한다.
첫째, 자산 분석과 정보시스템의 전반적인 현황을 파악하여 사례회사의 정보시스템을 파악하고, 체크리스트를 통하여 사례회사의 保安 상태를 파악한다.
둘째, 硏究의 성격은 探索的 硏究(Exploratory research)로 事例硏究를 통하여 정보시스템 자산의 위협에 대한 취약성을 평가하여 정보시스템의 保安對策을 재시 한다.
세째, 정보시스템 취약성 평가의 연구 대상인 정보시스템을 인사정책, 시스템 개발, 훈련1인식, 조직구조, 물리적 접근, 데이터와 프로그램 접근, 데이터 입/출력, 데이터 처리, 데이터베이스와 시스템 소프트웨어, (원격)통신, 터미널 사용, 환경, 백 엄과 복구의 13개 분야로 나누어 정보시스템 관리자를 통하여 평가하였다.
본 논문은 5章으로 構成되어 있으며 각 章의 範圍 및 內容은 다음과 같다.
第 1 章은 본 硏究의 전체적인 논지인 硏究目的, 硏究方法, 硏究範圍를 약술한다.
第 2 章은 정보시스템 취약성 평가를 위한 체크리스트 접근방법의 이론적 체계 를 구축한다. 이를 위하여 第 1 節에서는 정보시스템 危險1餘安 管理의 개념과 危險分析의 절차를 기술하였고, 第 2 장은 정보시스템 취약성 평가의 개념에 대해서 기술하였다.
第 3 章에서는 第 2 章에서 고찰된 개념을 근거로 해서 第 1 節에서는 정보시스템 危險分析의 일반적인 방법을 기술하였고,第 2節에서는 정보시스템 취약성 평 가를 위한 접근 방법으로 체크리스트 접근 방법과 소프트웨어 접근 방법을 제시하 였다. 第 3 節은 이 硏究의 방법인 체크리스 접근 방법 중 LLNL체크리스트의 구조 를 분석하였다.
第 4 章은 事例硏究의 방법과 결론을 설명하기위해 第 1 節에서는 사례회사의 정보시스템 현황을 파악하고, 第 2節에서는 사례회사의 정보시스템 자산 및 위협을 평가하고, 第 3 節에서는 班.NL체크리스트 접근방법을 통해 취약성을 평가하였다.
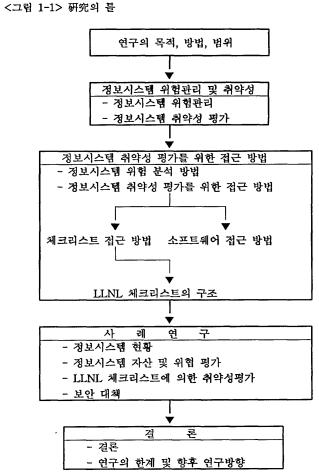
第 5 章은 결론 부분으로서 硏究의 결과를 요약하고 硏究의 한계점과 향후 硏究課題를 제시하였다. 이상에서 살펴 본 硏究의 構成과 內容은 다음 <그림 1-1>과 같은 연구의 틀로 요약될 수 있다.
第 2章 정보시스템 危險管理 및 취약성 평가
第 1 節 정보시스템 危險管理
정보시스템 危險管理, 혹은 保安管理, 혹은 危險分析에 대한 개념은 분명치않다. 그러나危險管理에 대한 개념에는 두가지 견해가 있다. <그림 2-1>과 같이 하나는 危險分析이 절차상 危險管理에 포함된다는 견해이고, 다른 하나는 서로 독립된 영 역으로 구분된다는 견해이다.
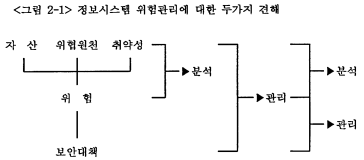
危險分析이란 정보시스템과 그 자산의 기밀성(confidentiality), 무결성(integrity), 가용성(availability), 기록성(accountability)에 영향을 미칠 수 있는 다양한 위협에 대해서 시스템이 취약함을 인식하고, 이로 인해서 예상되는 손실을 분석하는 것이 다. 危險管理란 불확실한 사건의 피해를 식별, 통제, 최소화하는 전반적인 절차에 관계된 경영과학의 한 분야로서, 정보기술餘安 危險管理는 측정/평가된 위험에 대한 안전정책을 일정 수준까지 유지/관리하는 것이다.이와 같이 窓鱉분석이 포함된 광의의 개념이 危險管理이고, 危險分析이 제외된 협의의 危險管理를 保安管理라고 하는 것이 타당할 것이다.
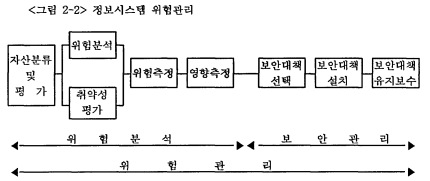
협의의 危險管理 개념과 관련해서, Robin Moses(1992)에 의하면, 危險管理의 목적은 危險分析 결과에 의해서 현재의 보안수준을 허용된 수준까지 높이기 위해서 保安對策을 마련하는 것이다. 다시 말해서, 정보시스템 危險管理는 경영층이 받아 들일 수 있는 수준까지 위협의 빈도와 영향을 감소시킬 수 있는 保安對策을 선택 하는 것이다. 그러나, 保安管理란 개념은 이보다 더 화장된 개념으로, 保安對策을 선택해서 설치한 후에, 유지1관리하는 것도 포함되는 것이다. <그림 2-2>는 정보시스템 위험관리, 위험분석, 보안관리의 개념을 도식화 한 것이다.
1979년에 미국 상무성 산하 NIST(National Institute of Standards and Technology)에서 발간한 FIPS Pub(Federal Information Processing Standards Publication) 65; Guideline for Automatic Data Processing Risk Assessment'에서 ALE(Annual Loss Exposure)를 근거로 자료처리에서의 위험에 대해서 기술한 바 있다. 1990년에 미국 법무성의 보안 및 비상기획국에서 준비한 危險分析지침으로서 'SRAG(Simplified Risk Analysis Guidelines)'는 NIST에서 다른 기관에서도 활용할 수 있도록 공표한 보안 지침이다. 여기서는 危險分析단계를 7단계로 구분하고, 危險 分析대상을 개인용컴퓨터, 응용시스템, 주전산기와 원격접근이 가능한 자동화된 시스템별로 구분하고, 이들을 다시 정보의 비밀성 여부와 민감성(sensitivity)에 따 라서 구분해서 기술했다.
1993년 EC(European Communities)에서 '危險分析'이라는 보고서가 발행했다. 여기서는 기존 66개 危險分析方法들을 분석하여 유럽 전체에서 공동으로 활용될 수 있는 분석방법을 개발하기 위해서 '요구구조(C淡m structure)'라는 도구를 개발 하여 유럽표준 뿐만 아니라 국제표준으로 발전시키려 하고 있다. 1994년 현재 국제 표준화기구(ISO: International Organization for Standardization)의 ISO/【EC(International Electromechanical Commission) JTC1/SC27에서 '정보기술보안 관리지침(GMITS; Guidelines for the Management of If Security)으로 危險分析 에 관한 표준화를 진행시키고 있다.
위에서 기술한 여러 기관의 보고서를 근거로 危險分析절차가 포함된 危驗管理과 정은 다음과 같다.
1) 자산 분류 및 평가: 보호해야 할 전산 자원들을 식별하고, 체계적인 분류를 해 서, 소유하고 있는 자산들의 가치를 평가하는 기본적인 단계이다. 여기서 자산이란 하드웨어, 소프트웨어, 데이터/데이터베이스, 사용자/전산요원, 시스템 관련문서, 전산자료 저장매체, 통신망 및 관련장비 등을 말한다.
2) 위협 평가: 위협(threat)은 자산(asset)에 해를 줄 수 있는 위험의 원천이다. 이와 같은 위협을 식별하고 분류해서, 발생빈도와 손실크기(혹은 강도(severity))를 측정하는 것을 말한다. 위협에는 위협원천에 따라, 자연재해로 인한 위협들(화재, 수재, 정전 등), 사람에 의한 의도적 위협들(단말기, 디스켓 등의 파괴 및 절취와 같은 물리적 공격, 그리고 시스템 자원의 불법사용, 허가되지 않은 자원의 불법접근, 타인으로 위장하여 권한사용, 바이러스, 벌레 등 유해프로그램 삽입과 같은 기술적 공격), 사람에 의한 비의도적 위협들(명령어 혹은 프로그램의 조작미숙 및 조작실수), 정보시스템의 결함(운용체제 결함, 응용프로그램의 결함, 통신 프로토콜 의 결함, 통신 소프트웨어의 결함)이 있다.
3) 취약성 평가: 취약성(vulnerability)이란 정보시스템에 손해를 끼치는 원인이 될 수 있는 조직, 절차, 인력관리, 행정, 하드웨어와 소프트웨어의 약점을 뜻한다. 이와 같은 약점을 확인하고 분류하여 위협을 감소시키는 것이 취약성을 평가하는 목적이다. 취약성에는 관리적 취약성(보안관리, 인원관리, 절차상관리, 사고대책관리 등에 대한 취약성), 기술적 취약성(하드웨어, 응용소프트웨어, 운영체계, 데이터베이스, 네트워크 등에 대한 취약성), 물리적 취약성(출입통제, 환경관리 등에 대한 취약성)이 있다.
4) 위험 측정: 자산에 대한 손실을 분석하는 과정으로서, 위협의 발생확률과 손 실크기를 곱해서 기대손실을 가능하면 계량적으로 계산한다. 손실크기를 화폐가치로 계산할 수 없으면, 정성적인 危險分析法을 이용한다.
5) 보안대책 선택: 평가된 위협요소와 취약요소에 대해서 保安對策(safeguard)을 선택하는 단계이며, 여기서 선택해서 추진하는 비용까지 계산해야 한다.
6) 비용효과 분석: 발생가능 한 위험요소에 대응해서 保安對策을 수립했을 경우 감소되는 위험수준을 화폐가치로 측정1평가한다.
第 2節 정보시스템 취약성 평가
취약성이 있다고 해서 곧 바로 손실을 입지는 않지만, 위협 요소들이 칩입 할 수 있는 근거를 제공하게 된다. 취약성 개념은 정보시스템에 대한 위험을 모형화 하는데 중요한 역할을 한다. 취약성 개념에는 일반적으로 다음과 같이 3가지가 있다.
첫째는 취약성을 '자산의 속성(attribute of assets)'으로 정의 하고 있다. Otwell과 Aldridge(1989)는 취약성을 "자산을 손상시켜서 위험을 일으키는 시스템의 성질" 이라고 했다. 보다 구체적으로 "시스템 내에서 불법적 상태로 변화되는데 소요되는 노며의 양(the amount of effort)에 대한 부적인 정도(inverse measure)" 라고 정의했다. Moses(1992)는 취약성을 "기존 시스템의 약점"이라고 했다.
둘째는 귀약성을 '자산과 위협의 관재(relationship between assets and threats)'로 파악하고 있다. Katzke(1988)는 취약성을 "자산, 위협, 保安對策, 保安對策臺과 간의 함수관계를 갖는 실체라고 정의했다. Schmidt(1988)는 취약 성을 "위협영향과 자산의 대응관계"로 파악하고, 취약성을 도출하기 위해서 다음과 같은 3가지 고려사항을 제시했다. 첫째는 자산이 위협 받을 가능성, 둘째는 자산이 위협에 의해 손상되는 정도, 세째는 繇安對策效果 이다.
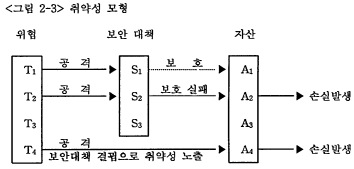
세째는 귀 약성을 '保安對策의 결핍(absence of safeguards)'으로 정의하고 있다. Guairo(1988)는 취약성을 "위협공격에 대한 통제 실패확률"이라고 했다. 시스템보안 연구위원회(1991)에서는 취약성을 "위협공격에 노출되어 있는 시스템의 상태" 라고 했다. Gilbert(1991)는 취약성을 "보안 대책시스템 내에 약점, 흑은 保安對策의 결핍"이라고 했다. Gilbert의 취약성 개념 측면에서 위험모형을 나타낸 것이 <그림 2-3>이다.
<그림 2-3>에서 위협 T1이 자산 Al을 공격했을 때, 자산 Al은 保安對策 S1에 의해서 보호되었다. 위협 T4가 자산 A4를 공격했을 때는 係安對策이 없어서 손실이 발생되는 경우이다. 그러나, 위협 T2이 자산 A2를 공격했을 때, 자산 A2는 保安對策 S2에 약점이 있어서 보호되지 못했다. 이와 같은 실패확률을 실제 정량적으로 추정하기는 어렵다. 그러므로, 본 硏究에서는 취약성 개념을 보안 대책시스템 내의 약점으로 보호실패 되는 경우는 제외하고, 단지 %安對策의 결핍상태라고 정의한다.
취약성 평가의 목적은 자산에 손실이 발생될 수 있는 약점을 식별하고 분류하여 위협을 감소시키는데 있다. Moses(1992)에 의하면, 취약성 평가(vulgar assessment)란 "식별된 위협원천에 의해서 손상될 수 있는 기존 시스템의 약점에 대한 심각성 수준을 식별하고 평가하는 것" 이라고 했다. 취약성 평가는 취약성에 대한 정의에 따라 그 방법이 달라질 수 있다. 단순히 '자산의 속성'으로만 정의하 면, 취약성을 정성적으로나 정량적으로 평가하기가 어렵다. '자산과 위협의 관계'로 정의하면, 관계에 대한 구체적 모형이 제시되어야 한다. 계량적인 평가모형을 도출 해도 실증적으로 적용하는데 는 위협발생 혹은 손실발생에 대한 확률추정을 해야 하는데, 이에 대한 과거자료를 확보한다는 것은 사실상 어려운 문제이다. 그러므로, 본 硏究에서는 취약성을 保安對策의 결핍상태로 정의하고, 취약성 평가를 保安對策의 유무를 식별하여, 保安對策이 결핍상태에 있는 경우 위협발생을 감소시킬 수 있는 保安對策을 제시하는 것이라고 정의한다.
Cooper(1989)는 전산자원의 환경에 따라 취약성을 물리적 취약성, 인적환경 취약성, 규제환경 취약성, 하드웨어 취약성, 소프트웨어 취약성, 네트워크 취약성으로 분류했다. 일반적으로 손실발생에 따라 물적 취약성(출입통제, 환경관리 등), 관리적 취약성(보안관리, 전산요원 및 이용자 관리, 보안정책 등의 문서화, 사고대책 관리 등), 기술적 취약성(하드웨어, 운영체제, 응용 소프트웨어, 네트워크, 데이터베이스 등)으로 분류할 수 있다.
이와같은 취약성의 영역에 따라서, Solms와 Eloff(1990)는 보안의 영역을 물적 보안, 논리적 보안, 경영 보안으로 구분했다. 세부적으로 물적 보안은 환경 보안, 물적 접근 보안, 물적 가용성 보안으로 구분 했고, 논리적 보안은 소프트웨어 보안, 데이터 보안, 통신 보안으로 구분 했고, 경영 보안은 관리적 보안, 인사 보안, 조직적 보안으로 구분 했다.
第 3章 정보시스템 취약성 평가를 위한 접근방법
第 1 節 정보시스템 위험분석방법
전통적인 危險分析方法에는 규범적 접근방법으로 위험선호(표용) 이론(risk preference (utility) theory)이 있다. 이외에도 평균-분산 효율성 기준 (mean-variance efficiency criterion), 파산확율(ruin probability), 통계적 이론분포를 이용하는 방법 등이 있다. 특히 정보기술에 대한 危險分析에서 방법에는 정량적 분석법과 정성적 분석법이 있다. 여기서 정량적 분석법이란 위협발생확률과 손실크기를 곱해서 계산하는 '기대가치분석(expected value analysis)인 경우이며, 정성적 분석법이란 손실크기를 화폐가치로 측정할 수 업어서 위험을 기술변수(descriptive variables)로 표현하는 경우이다.
정량적 분석법에는 수학공식접근법, 확률분포추정법, 점수법, 확률지배 (stochastic Dominance), 몬테칼로 시뮬레이션 등이 있고, 정성적 분석법에는 델파이법, 시나리오법, 순위결정법, 퍼지행렬법(fuzzy metrics), 질문서법(Questionnaires) 등 이다. 그리고, 복합적인 분석법으로 가치사슬분석(value chain analysis)이 있다.
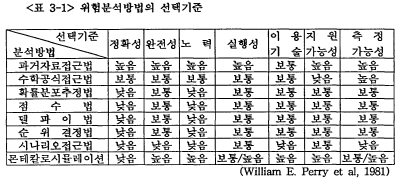
危險分析方法을 선택할 경우에는 비용, 복잡성, 적용성, 타당성 등을 고려하여 장 ·단점을 검토해야 한다. 危險分析方法들의 장 ·단점을 비교한 후에, PeW & Kuong(1981)이 제안한 다음과 같은 기준을 고려해서 그 분석방법을 선택하되 가능 하면 여러 방법을 복합적으로 사용하는 것이 바람직하다.
(1) 정확성;'위험분석방법에 의한 추정의 정확성 정도.
(2) 완전성: 분석1평가 과정 중 가능한 모든 위협속성을 포함시킨 정도.
(3) 노력: 위험을 분석하는데 소요되는 시간과 자원의량.
(4) 실행성: 위험분석 결과를 경영층이 받아들여 실행시키는 정도.
(5) 이용기술: 위험분석방법을 효과적으로 이용하는데 소요되는 훈련과 지식의 량.
(6) 지원가능성; 기대 손실을 추정하는 위험분석방법을 지원하는 명시적인 자료의 량.
(7) 측정가능성; 실제 손실과 추정 손실을 비교해서 추정 손실의 신뢰도를 높이는 손실 추정의 정확도.
분석방법들을 선택기준에 따라 정성적으로 높음, 보통, 낮음으로 평가한 것이 <표 3-1>이다. 높음은 선택기준의 목표에 아주 잘 도달된 것이고, 낮음은 그 반대 이다. 보통은 선택기준의 목표에 적절하게 도달된 것이다. 이와 같은 여러 가지 선택 기준들과 분석방법들의 장/단점을 고려해서 위험 분석자 혹은 경영자는 특정 상황 에 적절한 분석방법을 선택해야 한다. 분석방법에서 과거자료접근법은 미래 사건의 발생가능성을 예측하는 방법으로 사건에 대한 과거 자료를 이용하는 일상적인 기술통계분석을 의미하는 것으로 기대손실을 계산하고, 保安對策에 대한 비용효과에 따라 통제를 조정하는 방법이다. 정량적 분석법이 정성적인 분석법보다도 우수한 것은 당연하며, 특히 위협의 발생 빈도와 손실크기에 대한 과거자료가 있는 경우에는 과거자료접근법에 의해서 위험 측정이 가능하므로 대부분 선택기준에서 높게 평가되었다. 또한, 위에서 기술한 확률분포추정법, 점수법, 델파이법, 순위결정법, 시나리오접근법 등은 모두 주관적 접근법 이므로 낮게 평가되었다.
이와 같은 분석방법을 복합적으로 적용시키는 데는 Rainer, Snyder & Carr(1991)이 제안한 가치사슬분석(value chain analysis)이 이용될 수 있다. 위험분석과정별 적용 가능한 분석방법을 ( )안에 명시하였다.
단계1: 조직의 행위를 열거하기 위해서 가치사슬을 이용한다. (시나리오법 그리고/혹은 질문서법 + 델파이법)
단계2: 각 가치행위의 정보기술 구성요소를 열거하기 위해서 가치사슬을 이용한다. (시나리오법 그리고 질문서법 + 델파이법)
단계3: 가치행위 간의 연결을 열거하기 위해서, 그리고 각 연결을 지원 하는 정보기술을 결정하기 위해서 가치사슬을 이용한다. (시나리오법 그리고1혹은 질문서법 + 델파이법)
단계4: 조직 가치시스템을 검토하기 위해서, 그리고 내부 조직간 연결을 지원하는 정보기술을 지원하기 위해서 가치사슬을 이용한다. (시나리오법 그리고/혹은 질문서법 + 델파이법)
단계5: 열거된 정보기술자산의 가치를 결정한다. (정확한 화폐가치 부여 +델파이법)
단계6: 정보기술자산에 대한 가능한 위협들을 열거한다. (시나리오법 그리고/혹은 질문서법 +델파이법)
단계7: 잠재적 위협으로 부터 정보기술자산의 취약성을 결정한다. (정확한 숫자 부여 + 델파이법)
단계8: 조직에 대한 전번적인 정보기술 위험노출을 결정한다. (ALE 같은 수학공식접근법, 혹은 확률적 지배 이용)
이와 같은 가치사슬분석법은 경영층에게 정보기술자산에 대한 가치, 자산에 대 한 위협, 위협에 의한 손실발생확률 등을 고려하는 危險管理 프로그램에 대한 투자의 필요성을 논리적으로 이해 시키는데 큰 도움이 된다.
다음 페이지로